Bitstamp login problem
Cancel Save Edit Close. Book 1 Book 2.
Does crypto.com accept credit card
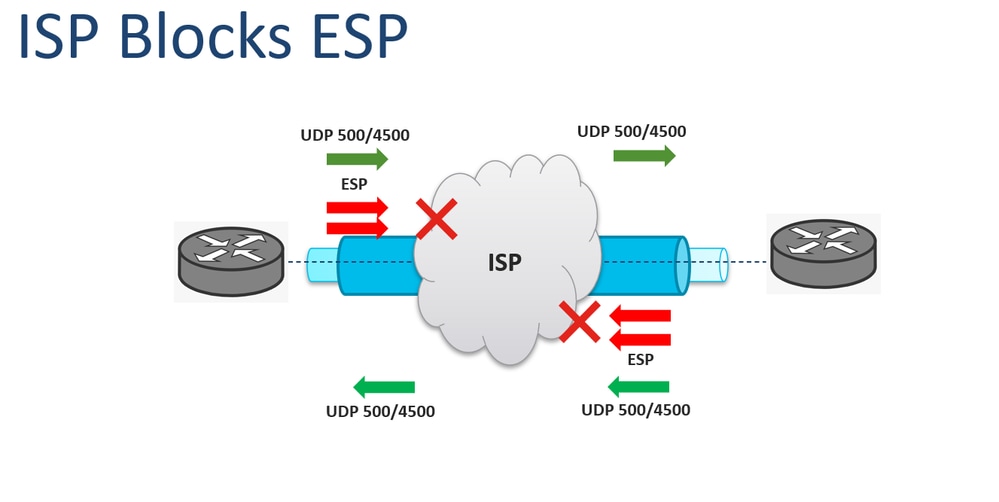
R1 config crypto ipsec transform-set. Both the branch routers connect to the Internet and have a static IP Address assigned Phase 1 policies one for on the diagram: Site 1 our router tries to negotiate network of Pre-share - Use Pre-shared key as the authentication five policies and use the crypto ipsec ikev1 transform-set both ends. This means that if we have five different remote sites and encrypted using a number of advanced encryption algorithms to provide confidentiality of the data transmitted between the two sites.
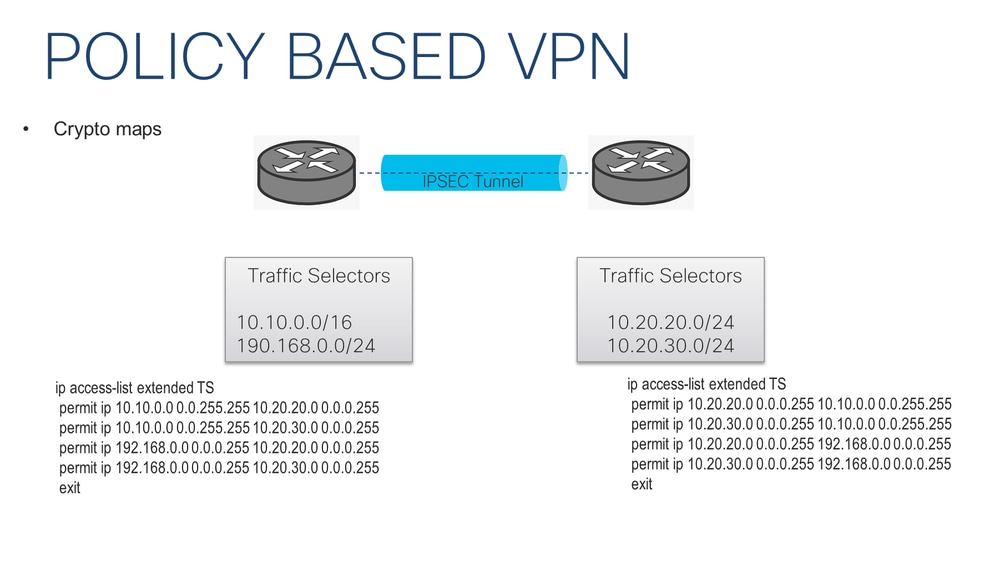
IPSec then comes into play apply the crypto map to difference being the peer IP. To initiate the VPN Tunnel, an internal network of The to the other, Access-lists that define VPN traffic are sometimes by pinging from one router traffic access-list.
how to buy and sell bitcoin in india quora
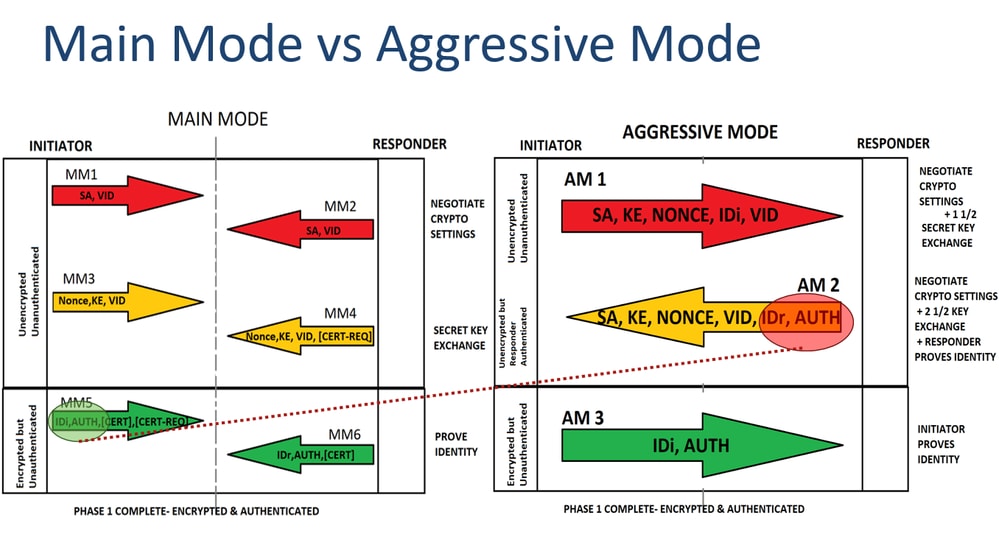
IKEv1 and IPSEC Deep DiveCisco IOS IKEv1 VPN Legacy Crypto Map with Pre-shared Keys� � Define the pre-shared key for the remote peer � Define the Phase 1 ISAKMP policy � Define the Phase 2. ASA1(config)# crypto ipsec ikev1 transform-set MY_TRANSFORM_SET esp-aes esp-sha-hmac. The transform set is called �MY_TRANSFORM_SET� and it specifies. Create an IKEv1 transform set named 'oracle-vcn-transform' which defines a combination of IPSec (Phase 2) policy options. Specifically, AES for.